Audit Log
In the modern-day dynamic world, managing data and change-induced implications is crucial. Keeping up with the need for ample data management, we have now introduced the Audit Log feature in the Gitea Enterprise. This comprehensive feature emphasizes providing an in-depth history of activities happening within your Gitea instances. Our latest feature captures a wide range of events like logging in/out, cloning a repository (including through SSH, HTTP), downloading the source code, downloading packages and so on.
Why the Audit Log Feature?
Audit Log feature for Gitea Enterprise offers a comprehensive logging solution that allows system administrators to keep track of various activities and changes. It ensures improved data security, compliance, accountability, and traceability.
User interface for Audit Log
Audit Log feature offers a neatly organized interface where you can easily access all the logs.
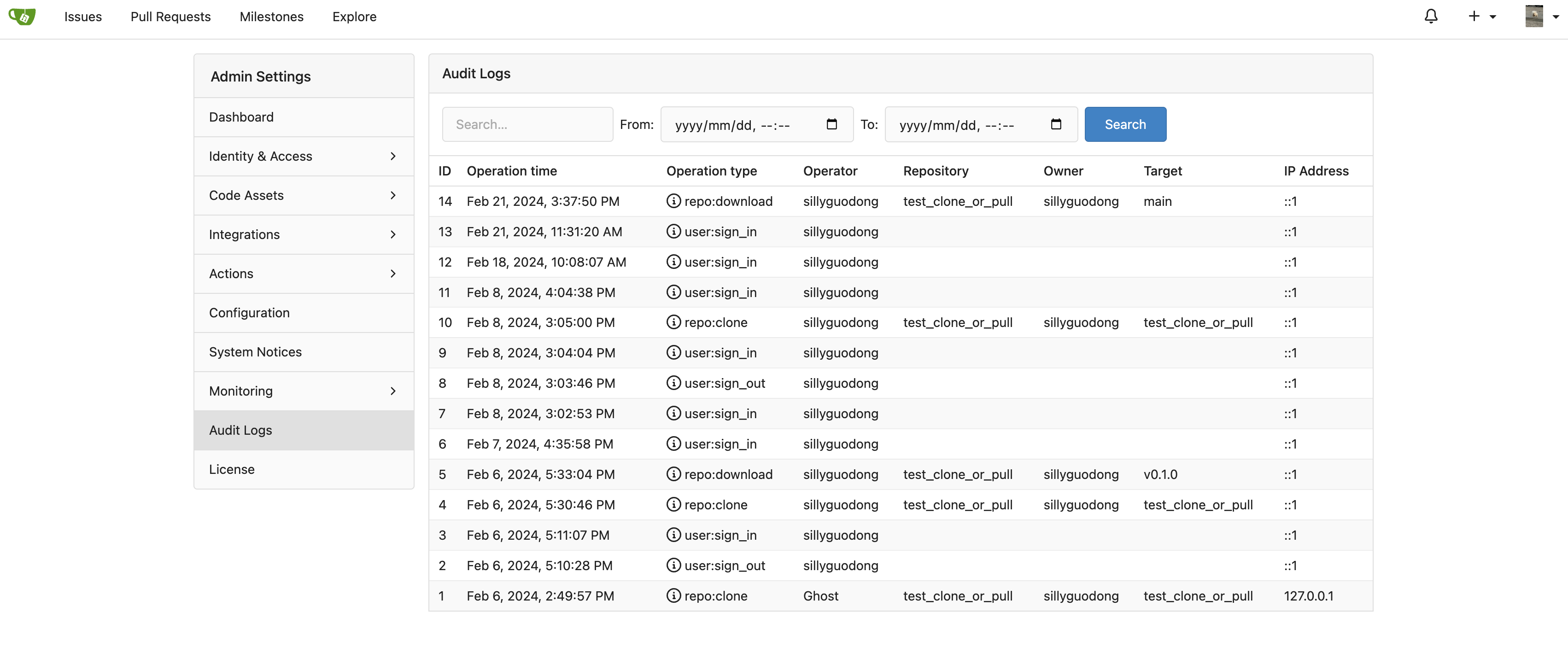
Let's talk about the content and organization of these records.
- Opeartion Time: This column displays the exact date and time at which an activity occurred. The details recorded can help track the sequence of operations and also aid in pinpointing activities within a specific timeline.
- Operation Type: Here you can find tags for different activities, like, 'user:sign_in', 'user:sign_out', 'repo:clone', etc. This column helps to identify the sort of task executed.
- Operator: This column records the Gitea username of the individual who performed the operation. This aids in accountability and backtracking of any unauthorized changes done.
- Repository: The Repository column indicates the specific repository related to the operation. This is particularly useful in identifying the source/object related to the performed operation.
- Owner: The Owner column does not necessarily denote the owner of the repository in question; it refers to the entity that owns the object involved in the operation. Depending on the operation type, the owner could differ. In case of opeartion like 'Download package', where a package does not expressly belong to any repository but has an independent owner, this field will capture that owner's details.
- Target: Specifically, this denotes the specific object or individual that an operation was directed at. For example, in a file download situation, the target would be the file name.
- IP Address*: The IP address from where the operation was performed is also logged. This can provide extra security measures as it allows the tracing of the geographical location of operation execution.
What operations are logged in the audit log?
- Sign in/out: This operation records an instance when a user authenticates into or logs out of their Gitea account. It provides the date and time of the activity, the user involved in the operation, and the IP address. This maintains accountability and helps secure events around user access.
- Git clone/pull (both HTTP and SSH): This involves recording instances when a user clones (creates a copy of the repository on their local machine) or pulls (fetches the newest updates from a remote repository) in both HTTP and SSH. The Audit Log captures the method used (HTTP or built-in SSH Server), the IP address, the repository involved, and of course, the operator and operation time. This enables tracking and managing codebase access.
- Download the source code of repository: In events of source code downloads from a repository, the Audit Log entry signifies the user performing the opeartion, the targeted repository, the operation time, and the IP address from where the operation was conducted. This provides insights on the distribution of your source code.
- Download package: This logs instances where a software package is downloaded. The Audit Log records the package's owner, the operator who downloaded it, the operation time, and the IP from where the download was initiated. This operation helps in monitoring and managing the dissemination of resources present in the Gitea instance.
Conclusion
The new Audit Log feature brings enhanced security and operational transparency to the Gitea Enterprise. By offering an exhaustive report of who did what and when within your Gitea environment, it helps preventing unauthorized operations and ensures compliance with the necessary data protection regulations.